A number of years ago your company provided me with a 3-person team to completely re-do the SAP security for the company I was employed by at the time and I. Click on create role button.

Identity Management And Sap Users Roles And Transactions Part1 Ibm Security Identity And Access
Sep 13 2006 at 1224 PM.

. This guides explains the new role development framework for SAP HANA using XS Advanced and HDI. Our implementation methodology is closely aligned with the SAP ASAP methodology but is. SAP Security Job Description.
Indirect Assign roles to a Position. The functional teams can use the security matrix to assist in adding theroles to their BPPs business process procedures. Security and Role Design Service The regulatory and compliance landscape of today requires companies to ensure critical business applications such as SAP are properly secured and adhere to stringent guidelines related to privacy proper segregation of duties and limiting access to sensitive business and system transactions in order to prevent financial.
Sap-security SAP Role Design Recommended Approach. Number of authorization objects in assigned roles. Enter new role id that you want to create In this configuration we are going to create Z_ROLE_USER with certain transaction codes authorizations.
On Role maintenance screen update the following details. Number of duplicated transaction codes in roles. The client to design and implement a new SAP security design following our tier 4 methodology.
The SAST SUITE role template with roles in a modular architecture. Basic knowledge of SOX and the implementation of controls in the Access Control Space. SAP Provisioning can be handled in different ways.
Business processes and Role based Authorization Concept. Engaging RBP consultant and RBP Business Owner during EC Design. Proficient in IT general controls and SOX requirements as they relate to security administration.
SAP System Security in Unix and Windows Platform Single Sign-On Concept So the security in SAP system is required in a distributed environment and you need to be sure that your data and processes support your business needs without allowing unauthorized access to critical information. To assist you in ensuring the security of your SAP Business ByDesign solution we provide this Security Guide. Number of SAP roles to be built ie new roles may be a clean slate with regard to mitigation of security risks created to solve existing SoD conflicts which often fails prior to go-live to address the root causes for SoD conflicts.
I like to stick to the KISS principle in security design - keep it simple. It gives recommendations and provides examples on how to best build roles. Number of changed and manually-inserted authorization objects.
However SAP also designs composite roles that contain one or a few single roles. I would not recommend the master derived approach since you indicated that it is a small company and you are unlikely to need to create derived roles. Result in loss of information or processing time.
SAP provisioning is the process of assigning SAP roles to the SAP User ID. Let us explore the technical and business reasons for exploring composite roles. We combine our Packaged Role Design with our sophisticated Security Role implementation methodology to provide our customers with a proven approach that ensures a high quality cost effective and low maintenance design that is both easily sustainable and scaleable.
Surviving an SAP Audit. The document also covers the below topics that play a crucial role in the RBP security design. Separate access for specific admin roles.
Basic SAP CUA security and authorization concepts knowledge ECC BI PIPO. You get a role menu whose structure is usually similar to that of the SAP menu. With a double click on the single role you can view a role description.
- describe SAP security roles and translate their contents transactions included into Business Tasks business language for Role Owners - Role Owners would review this document before approving any role changes and also potentially depending on document content educate themselves on conflicting roles from SOD. The implementation of the new SAP security design helped this client reduce the number of roles in the SAP environment which combined with the SAP GRC Access Controls application facilitated the overall user provisioning processes. Enter transaction code PFCG in the SAP command field and enter.
Limiting number of users with access to manage RBPs. Vote up 0 Vote down. The roles are delivered with a standardized specification of the documentation structure in the role long text.
University degree with strong SAP background. We use cookies and similar technologies to give you a better experience. Best practices and examples for developing roles in SAP HANALearn about building HDI containers and their setup create design-tiem objects in MDC and about granular roles adminstration roles security roles and support roles Download the Document.
The HR team will assign a user to a position. Below are example benchmarks for examining an SAP. A user can inherit access directly or indirectly.
In the course of creating a role the PFCG initial screen enables to select either a single or composite role. You can display the list of assigned single roles for each of these composite roles in the backend system in transaction PFCG. 23 Document Structure The Security Guide contains the following sections.
Minimum of 5 years experience with SAP Security concepts Role Profile Auth Objects etc The person in this position needs to move about inside office to access file cabinets office machinery etc. The Security Matrix helps to view the roles in an easy-to-read format and helps the SAP Security Team communicate to the functional teams the security roles being configured. We provide the single roles that cover the major functions of SAP S4HANA and SAP ERP.
These security requirements apply equally to SAP Cloud solutions. RBP Reports and Change Audit Reports. The objective of this document would be to.
A Practical Guide to SAP Audithttpsamznto2O1cDK6Security Audit and Control Features SAP ERP 4th EditioNhttpsamznto2K3UUR8. It gives recommendations and provides examples on how to best build roles. AJ I would also gently suggest getting into contact with one of your counterparts from the Ernst Young Cleveland office.
The BPPs are used for building training and integration testing. Direct Assign roles directly to users. A single role is an integration of t codes and authorization objects.
Implementing a strong Security strategy with policy adherence is requisite to manage compliance minimize risks and to setup a secure and efficient authorization concept with process efficiency and adoption which can be based on organizational structures. In a SAP system human errors negligence. The following activities should be conducted.
Enter the name of the composite role for example SAP_MARKETING_EXPERT click on Display and then select the tab Roles. Best practices and examples for developing roles in SAP HANA. Number of roles with transaction code ranges or wildcards.

Hr Resume Writing Guide And Tips Hr Resume Professional Resume Examples Job Resume
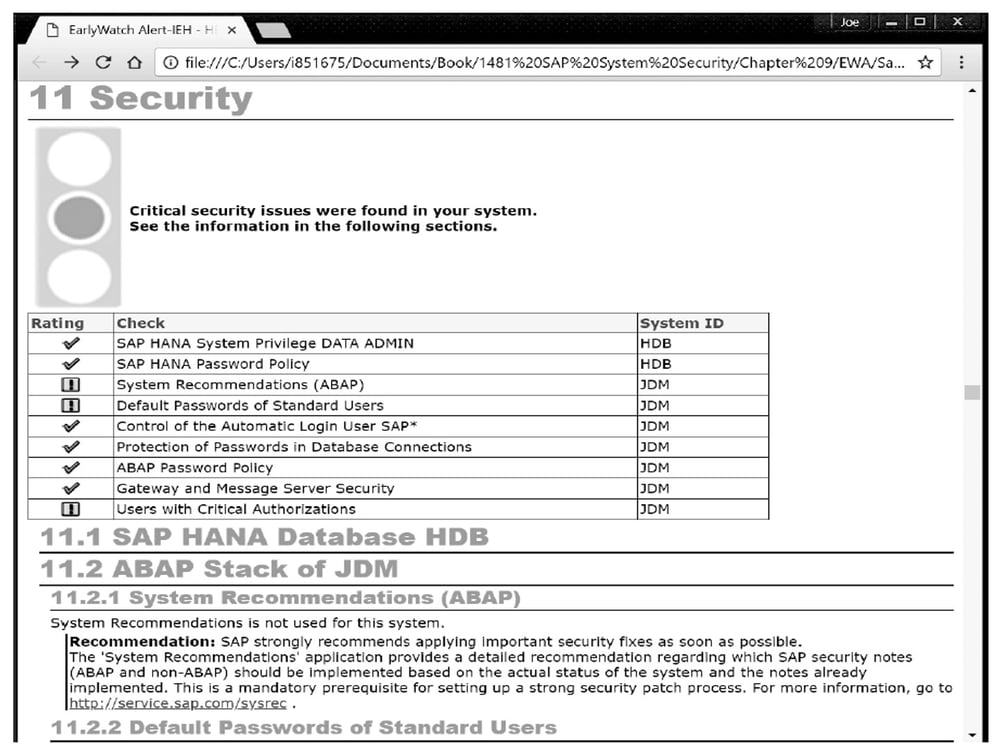
The Definitive Guide To Sap Security Sap Press

Transaction To Role Mapping Sap Blogs
Sap Security Tutorial For Beginners Dnsstuff

How To Create A Data Backup Plan To Improve Your It Security Download This Data Backup Plan Standard If You Are Working O Data Backup Data Masking How To Plan

Sap S 4hana Authorizations Sap Blogs


0 comments
Post a Comment